All contest are free!! Need registration.
Contestant does not need CODE BLUE conference ticket, can access only contest area.
If you want to attend contest, please register at each contest registration form.
Each contest organizer will explain you about contest admission.
| Contest Schedule | ||||
|---|---|---|---|---|
| Contest | Duration | Registration | ||
| Practical CAN bus hacking | 11/9. 10:00-12:00,13:00-17:00 11/10 10:00-12:00,13:00-16:00 |
Pre-registration | ||
| Hack2Win | 11/9 10:00 - 18:00 11/10 10:00 - 16:00 |
On site | ||
| CODE BLUE CTF | 11/9 10:00 - 11/10 16:00 | Pre-registration | ||
| Ghost in The Shell CTF | 11/10 10:15 - 17:15 | Pre-registration | ||
| ICS CTF | 11/9 10:00 - 18:00 11/10 10:00 - 16:00 |
Pre-registration | ||
| F-Secure RDS Hacking Challenge | 11/9 10:00 - 18:00 11/10 10:00 - 16:00 |
On site | ||

Practical CAN bus hacking by White Motion & Quarkslab
Have you ever tried to hack a CAN bus for real? What do you think? Is it hard or easy? Do you need expensive devices? To find out the answers, play our CTF, try by yourself and take the control of our RC car and its two ECUs!
Registration:Registration Form (Registration Closed)
Practical CAN bus hacking
Registration:
Registration Form(Registration Closed)
Rules:
The teams have to take control of a RC-car by exploiting vulnerabilities in its ECUs or via the CAN bus.
Maximum of 5 teams at the same time
A car prototype containing the ECUs will be provided to each team, as well as some documentation on the possible attacks.
During the game, each team will study the documentation and try to get into the car's ECUs to take its control.
When a team has found a way to take control of it car prototype, one can check it on a real Tamiya 1/10 RC-car and get the points.
Things to bring:
PC, LAN cable, etc.
# The competition environment is connected by wireless LAN (Wired LAN as a backup is available). Bring your own PC and equipment that can be connected to both.
Prize:
The Winner get a prize.
Registration:
To register to the CTF, follow this link : Registration Form(Close)
2017/11/8 update
Reception time:
Starts at 9:30 AM
Opening time:
11/9 10:00-18:00
11/10 10:00-16:00
Things to bring:
1:If you have any specific tool you want to use as attacking tool (Send and Receive CAN Extended ID messages), please bring it with you.
2:Laptop with USB Type-A interface
#If you choose the Raspberry Pi as attacking tool, you don't need to bring anything. Please note that we only have 6 Raspberry Pi, so one team may need to use another tool than Raspberry Pi.
Notes:
-We have 15 registrations now, and 7 teams can play at the same time. You can play in order of arrival. If there is a team waiting, there will be team rotation. The rotation will depend on time spent playing and challenge progression. (Roughly 1 to 2 hours as guide.)
-We have prepared 6 Raspberry Pi, 2 HydraBus, 1 Teensy, and 1 Macchina as attacking tools.

Hack2Win by BeyondSecurity
Script kiddie? Hacker? Pentester? Robot?
Come show your skills at Hack2Win.
Hack2Win is a hacking competition sponsored by Beyond Security vulnerability disclosure program - SecuriTeam Secure Disclosure (SSD)
Hack the target -> win the money.
First prize - 10,000$ USD and total prizes for�� this contest are $50,000 USD!
Are you up to the challenge?
Hack2Win
How to Participate:
Just come and run your exploit!
No need to register!
Hack2Win - is a hacking competition we started at Code Blue 2015.
This year we have changed the format, raised the difficulty level and increased the prizes.
The goal of the event is to find who can gain the highest privileges on any of the target software and hardware.
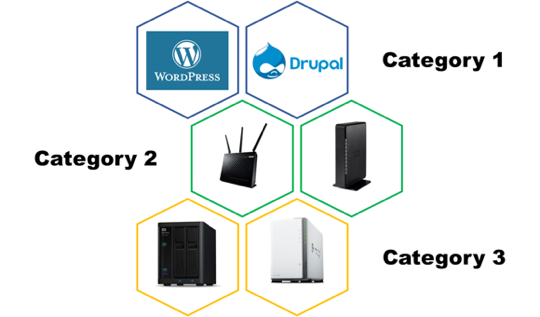
In the new format we have:
- 3 categories, in each category we will have a 2 products from different vendors
- Each category has different payouts
- Each category has only one first place winner
- A Quadcopter will be given to one participant who will be ?the best of the show?
================================================
Targets:
================================================
Category 1 - CMS
WordPress default installation with the following plugins(*):
- Really Simple CAPTCHA
- Contact Form 7
- WooCommerce
- Google XML Sitemaps
- Yoast SEO
- All in One SEO Pack
- Akismet
- Wordfence Security
- W3 Total Cache
- NextGEN Gallery - WordPress Gallery Plugin
- Page Builder by SiteOrigin
- Advanced Custom Fields
- Ninja Forms - The Easy and Powerful Forms Builder
- MailChimp for WordPress
(*) Each of those plugins has at least 900K active installations
Drupal default installation with the following plugins(**):
- Chaos tool suite (ctools)
- Token
- Pathauto
- Webform
(**) Each of those plugins has at least 500K active installations
Category 2 - Routers
- Cisco RV132W Wireless-N VPN Router
- Asus - RT-AC68U
Category 3 - NAS
- Western Digital - My Cloud Pro Series PR2100
- Synology - DiskStation DS216j
================================================
Prizes:
================================================
Category 1 and 2:
- WAN RCE - 10,000$ USD
- LAN RCE / Information disclosure that leads to password disclosure / Authentication bypass - 5,000$ USD
- Rest password - 2,500$ USD
Category 3:
- WAN RCE - 5,000$ USD
- LAN RCE / Information disclosure that leads to password disclosure / Authentication bypass - 2,500$ USD
- Rest password - 1,250$ USD
================================================
Contest Rules:
================================================
Judging Criteria
- New - the attack uses an unknown vulnerability (no record of it can be found on Google, Exploit-DB, etc)
- Complex - what was required to reach a successful attack
- Innovative - we regard an RCE as more innovative than SQLi, for example
- LAN or WAN - more points if the attack comes from the WAN side
- What is gained - we give no initial access to the challengers, so any type of access is an achievement. Of course, a guest level access would be considered less valuable than root
- Write-up Quality - how well is the write up (in English): including details, explanations, etc
Device Settings
- All the devices will be factory reset - i.e. default settings, and the only non-default setting would be the password for the ?admin? (or equivalent) account as documented in the product?s user guide, and the WiFi password (if applicable).
What counts as "hacked"
- A device would be considered "hacked" if the participant can prove they:
- Gained access to the device's post-authentication admin web interface (remember - you will not be given any credentials)
- Changed some configuration value, like the WiFi password
- Made the device do something it?s not supposed to do: like execute code, or open a port/service which was previously closed (like SSH, telnet, etc)
What we won't count as a "hacked"
- Causing a malfunction to the device, DoS / XSS / CSRF, making it unresponsive, making it no longer boot, etc
- Usage of any known method of hacking - known methods including anything that we can find on Google/Bing/exploit-db/etc ? this includes: documented default password (that cannot be changed), known vulnerabilities/security holes
Eligibility
- The contest is open to anyone who is at the legal age to receive a contest prize in your country, if you are not allowed to receive prizes - and please make sure to check this before participating - you may want to team up with a person that is eligible.
- The contest is not allowed to anyone working for one of the vendors, or is involved in development of the above devices.

CODE BLUE CTF by binja & TokyoWesterns
CODE BLUE CTF organized by Japanese top player.
Online Registration(https://score.ctf.codeblue.jp/)
CODE BLUE CTF
Registration:
Registration Form(On-site Registration Closed)
Online Registration(https://score.ctf.codeblue.jp/)
In modern times the Internet is the vital of our society, which inevitably brings about cyber crimes, increasing in number and quantity. In late years the importance of information security is getting recognized with reports on an attack toward a specific organization or the rapid prevalence of IoT devices, but when it comes to highly-sophisticated invasion, few people understand the way of causing and consequently guarding against it.
To deal with this problem, many overseas security conferences try organizing CTF to extend the knowledge and understanding of state-of-the-art attack techniques and countermeasures.
However, none of International conference in Japan has ever had this trial although some Japanese people have held CTFs up to now. This year we CODE BLUE decided to establish our own CTF powered by top Japanese CTF players, with the aim of improving the situation.
On the other hand, CODE BLUE CTF is also the project which binja and TokyoWesterns, the host of this CTF launched in order to purely pursue what is "Exciting CTF". They believe people should not forget the appealing and enjoyable aspects of CTF despite the fact that CTF is for the purpose of research and the development of ability. Through this CTF, they hope to give you the opportunity to deepen your understanding of advanced subjects while having fun with a number of challenging and interesting problems.
Rule:
Jeopardy(You can play CTF online and onsite both)
URL for registration page will be announced before the conference.
Date:
11/9(Thu) 10:00 +0900 - 11/10(Fri) 16:00 +0900
Prize:
We will invite the team that gets 1st place among onsite teams to the networking party held after the closing ceremony.

Ghost in the Shell REALIZE PROJECT x SECCON CTF for GIRLS in CODE BLUE
On November 10th, CTF for GIRLS will jointly hold international female-only CTF with "Ghost in the Shell REALIZE PROJECT" at the CODEBLUE 2017. "Ghost in the Shell" is the famous science fiction comic which is originally written by Shirow Masamune , and was made into movie by Hollywood in 2017. "Ghost in the Shell REALIZE PROJECT" is the project which goal is to realize and materialize the technology and worldview of the "Ghost in the Shell".
The ultimate goal of the Ghost in the Shell CTF is to produce highly skilled female security engineer, such as Motoko Kusanagi, the heroine of "Ghost in the Shell" which is called as "ultra-wizard hacker", from our CTF.
In addition, in the Ghost in the Shell CTF, there will be a "Ghost in the Shell-style" CTF visualization system called "AMATERAS ZERO", which is developed by National Institute of Information and Communications Technology(NICT).
Ghost in the Shell REALIZE PROJECT x SECCON CTF for GIRLS in CODE BLUE
Registration:
Registration Form(Registration Closed)
Date :
2017/11/10(Fri) 10:15am - 5:15pm (Reception Opens from 9:00am) (JST)
Venue :
BELLESALLE Shinjuku Grand 5F Room K, 8-17-1 Nishi-Shinjuku, Tokyo, Japan, 160-0023
Access :
https://codeblue.jp/2017/access_map/
Requirement : Female-only
CTF Style : Jeopardy-style CTF & Individual CTF
Hosted by :
GHOST IN THE SHELL REALIZE PROJECT,
SECCON Executive Committee / CTF for GIRLS
Japan Network Security Association (JNSA)
Special Sponsor :
National Institute of Information and Communications Technology (NICT),
Lac Co., Ltd
Supported by: CODEBLUE
- Ghost in the Shell REALIZE PROJECT Official Web Site
- SECCON Official Web Site Contest page
*CTF (Capture The Flag) is information security competitions.

ICS CTF by Red Alert Team (NSHC)
It is a SCADA CTF with the scenario and simulation.
We will also provide the attack tool kit while playing CTF.
ICS CTF
Registration:
Registration Form
Date:
11/09(Thu) 10:00 - 18:00
11/10(Fri) 10:00 - 16:00
We have 6 scenarios in different environments to understand threats of real ICS world with our various experience in pen-testing, incident response, and bug hunting. This CTF will be helpful from beginner to ICT expert as well.
Challenge Category
- Bypass Airgap
- ICS Protocol
- PLC & HMI
- Forensics
- Cyber Incidents
- Critical Industrial Infrastructure
Rule:
1.All challenges in our CTF is scenario based and have different point
2.Some challenges have hints to lose different point
3.It is prohibited to share keys or solution with other teams.
4.Most key should be submitted on the web site.
5.You may demonstrate for some challenges to judges.
6.Examination for Demonstration is limited for 20 mins per team.
7.We will provide attack tool kit (not including laptop) only while playing CTF
8.If you find any bug in this system, let us know.
9.You can be disqualified if our staff know you attack our system or break rules
Preparations for CTF:
We will provide attack tool kit (worth $600) to bypass airgap (RF, Bluetooth, USB based microcontroller, Wifi), but not including:
- Kali linux
-Analysis Tools (ex Wireshark, Burp, IDA, Olly ..)
Prizes for Winner:
TBD

F-Secure RDS Hacking Challenge
F-Secure Rapid Detection Service (RDS) helps prepare your organization for advanced cyber-attacks, before and after they happen.
Attempt to exploit, pivot, and elevate privileges in a network of Windows and Linux virtual machines without being detected by RDS. You win, if it is not detected by RDS within the time limit.
We are waiting for your challenge.
F-Secure RDS Hacking Challenge
Registration:
No preregistration is necessary. Please come to the venue.
Date:
11/09(Thu) 10:00 - 18:00
11/10(Fri) 10:00 - 16:00
F-Secure Corporation is a global cyber security and privacy company based in Helsinki, Finland.
Our new product, named Rapid Detection Service (RDS) helps prepare your organization for advanced cyber-attacks, before and after they happen. This fully managed service is designed to detect the most skilled of attackers, whether they're using malware or non-malware tactics, techniques, and procedures. It enables you to respond to threats promptly, with actionable guidance from our experts.
At the venue, please try to hack Windows and Linux virtual machines on the network. You win, if it is not detected by RDS within the time limit.
Let's try it!
Rule:
1.Attempt to exploit, pivot, and elevate privileges in a network of Windows and Linux virtual machines without being detected by RDS. You win, if it is not detected by RDS within the time limit.
2.You can try it either by individual or by team.
3.20 Minute Time Limit per contestant / team. You may continue to try to hack undetected for up to 20 minutes, even if we detect your earlier attempts.
4.We will provide many standard tools on the workstation,
5.At minimum, we will pre-load the following:
- Out-of-the box Kali Linux virtual machine and tools
- Metasploit and Armitage UI
- A Metasploit Meterpreter Payload for establishing the first foothold onto a virtual workstation
6.but you may also bring your own on a USB memory to be loaded on the system.
- e.g. : Windows scripts / binaries targeting Windows 7 (x64), Windows 10 (x64), Windows Server 2012 R2 (x64) ; Linux scripts / binaries for use on Kali Linux 2017.01 (x64) ; Personal memos and notes, and etc.
7.Scoring will be explained at the venue.
Prize :
1st Place: Amazon Gift Card (JPY50,000)
2nd Place: To be announced at the venue.
3rd Place: To be announced at the venue.